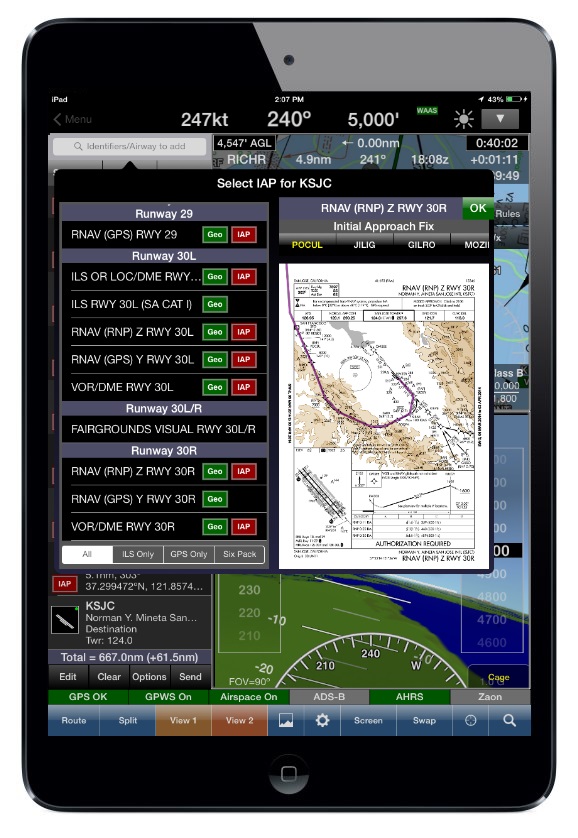
The study was produced by a group of computer scientists from the University of California,University ofSan Diego [sic.] and Johns Hopkins University. The group examined three combinations of devices and apps most commonly used by GA pilots, including; the Appareo Stratus 2 receiver with the ForeFlight iPad app; the Garmin GDL 39 receiver with the Garmin Pilot iPad app; and the SageTech Clarity CL01 with the WingX Pro7 iPad app. This popular combination of a receiver paired with an iPad and app is referred to as a Mobile Cockpit Information System (MCIS) by the research group.When used in-flight, depending on the aeronautical information services supported by the receiver, these devices and apps give GA pilots access to Flight Information System-Broadcast (FIS-B), a data broadcasting service that works with Automatic Dependent Service-Broadcast (ADS-B) ground stations to provide weather and airspace restrictions, among other information, through a data link to the cockpit. Pilots can also use them to access the Traffic Information System-Broadcast(TIS-B) service offered to ADS-B users as well. The information is obtained by the receiver and displayed via the application interface on the iPad to the pilot."We found a number of vulnerabilities that would allow an attacker to manipulate information that a pilot would see on the iPad that we think are serious," Kirill Levchenko, a computer scientist at the Jacobs School of Engineering at UC San Diego, told Avionics Magazine.
During testing, researchers found significant safety flaws in all three systems. Two of the systems allowed an attacker to replace completely the firmware, which is home to the programs controlling the devices. The Appareo Stratus 2 allowed the firmware to be downgraded to any older version. All three devices allowed an attacker to tamper with the communication between receiver and tablet. Both types of attacks give an attacker full control over safety-critical real-time information shown to the pilot.
By tampering with the aircraft position, altitude, and direction indications, also known as heading, as well as weather data and positions of other aircraft displayed to the pilot, an attacker can deceive the pilot, leading them to take actions detrimental to flight safety. Factors such as visibility and pilot workload increase the likelihood of a catastrophic outcome. For example, misrepresenting aircraft position during final approach in poor weather could result in a collision with other aircraft or a crash into nearby terrain.
Two of the systems allowed an attacker to replace completely the firmware, which is home to the programs controlling the devices.
Researchers point to several secure design practices that can remedy the flaws they identified. Among them, cryptographically securing communication between receiver and tablet, pairing the receiver with the tablet (in the same way that Apple smart phones are paired with specific computers), signing firmware updates and requiring explicit user interaction before updating device firmware. Data such as maps and approach procedures should be downloaded to the tablet using HTTPS or digitally signed by the vendor.
Most of the systems are fairly new to the market, researchers point out. “It’s a great time to make them secure from the get-go,” Levchenko said.
In addition to Levchenko, co-authors on the paper are UC San Diego computer science Ph.D. students Devin Lundberg, Brown Farinholt, Edward Sullivan and Ryan Mast, UC San Diego computer science professors Stefan Savage and Alex C. Snoeren, as well as Johns Hopkins computer science professor Stephen Checkoway. Lundberg is the first author on the paper.
This work was supported by the National Science Foundation grant NSF-0963702 and by generous research, operational and/or in-kind support from the UC San Diego Center for Networked Systems (CNS).
Devin Lundberg, Brown Farinholt, Edward Sullivan, Ryan Mast,
Stephen Checkoway, Stefan Savage, Alex C. Snoeren, and Kirill Levchenko, “On
The Security of Mobile Cockpit Information Systems” UC San Diego, Johns Hopkins
University. In M. Yung and N. Li, eds., Proceedings of CCS 2014. ACM Press, Nov. 2014.
ABSTRACT
Recent trends in aviation have led many general aviation
pilots to adopt the use of iPads (or other tablets) in the cockpit. While
initially used to display static charts and documents, uses have expanded to
include live data such as weather and traffic information that is used to make
flight decisions. Because the tablet and any connected devices are not a part
of the onboard systems, they are not currently subject to the software
reliability standards applied to avionics. In this paper, we create a risk
model for electronic threats against mobile cockpit information systems and
evaluate three such systems popular with general aviation pilots today:
 |
| Appareo Stratus 2 Receiver |
 |
| WingX Pro7 app |
 |
| Garmin Pilot App |
- The Appareo Stratus 2 receiver with the ForeFlight app,
- the Garmin GDL 39 receiver with the Garmin Pilot app, and
- the SageTech Clarity CL01 with the WingX Pro7 app.
We
found all three to be vulnerable, allowing an attacker to manipulate
information presented to the pilot, which in some scenarios would lead to
catastrophic outcomes. Finally, we provide recommendations for securing such
systems.
Author References
a member of
- the Johns Hopkins University Information Security Institute (JHUISI)
- the Center for Automotive Embedded System Security—a collaboration between UC San Diego and the University of Washington.
- faculty in the Health and Medical Security lab
- Trustworthy Health and Wellness (THaW), co-principal investigator, a collaboration between JHU, Dartmouth College, the University of Illinois, and the University of Michigan.


No comments:
Post a Comment